1: How Did It Happen? Well, Why Did Your Car With The Top Down, Keys In, Parked in Da Hood Get Stolen?
First, here’s Charlie Martin on why it happened:
Someone, somewhere, decided that they didn’t want to spend the money: undoubtedly they had budget constraints.
So the sensitivity of the data wasn’t properly identified, passwords were used instead of a stronger scheme, the systems involved had “superuser” or “root” accounts that by definition have access to everything, and the users who had access to those root accounts were Chinese nationals in China, who — I think we can fairly say — didn’t meet the U.S. government’s standards for computer security.
Perhaps the biggest issue of all is that the government had centralized the collection of that data into a single web-based system, e-QIP, which means that all this data was collected in one place.
I would bet money that each of these decisions came down to someone saying: “Oh, that’s too hard,” “Hiring offshore workers is cheaper,” “That’s too inconvenient.”
At each of those steps, some security was lost because someone decided it was easier to relax the requirements than to get the more expensive and annoying solution. And while the inspector general was calling out the hazards, no one was willing to rock the boat.
It’s worth it to Read The Whole Thing™ — Charlie’s been around long enough to see a Death March software project or two — but the bottom line seems to be, because OPM secured it like the Last Guy Still Using AOL® secured his cute-kitten .jpg files.
2: Nobody Knows How Big The Numbers Are — Because Execs Are Lying
Second, there are some new numbers, and we’re expecting the release of even larger numbers Friday (too late for the evening news). We’ve seen the numbers build from 2.9 to 4 to 14 to 18 to 29 to 32 Million. It gets hazy fast. For instance:
- OPM Director Katharine (“Fat, Incompetent and Stupid is so a way to go through life”) Archuleta, selected for that job by the usual process of Washington racial/ethnic/sex beancounting, insisted that the agency’s final number was 4.2 million. At the same hearing, an FBI officer, Acting Assistant Director for Cyber James Trainor, stood by the Bureau’s 18 million estimate, briefed earlier to Senators by FBI Director James Comey. Trainor, unlike Archuleta, showed his work: an OPM memo, exposing Archuleta as either an incomptent, a liar, or (the smart money says) an incompetent liar.
- House Oversight Chairman Jason Chaffetz, R-Utah, brought up the 32 million number. However, that’s just the cleared personnel and applicants that OPM has mishandled data for; each person’s 150-page questionnaire or electronic equivalent also exposes the data of numerous other persons (references, employers and supervisors, family members, foreign friends) and, more alarmingly yet, the threads that form the skein of relationships of all those people have also been exposed to a hostile intelligence service.
Of course, their defense is, they’re not lying, they’re just so wrapped up in their own red tape they can’t generate diddly.
But the bottom line is this: if you have completed an SF 86 paper security questionnaire or the replacement Electronic Personnel Security Questionnaire (EPSQ) on e-QIP at any time since the early or mid-1980s, you had best assume your secrets are secrets no more.
OPM did not investigate all DOE clearances, so if you had a nuclear clearance but not a DOD one, your information may be safe.
3: They Say They’re Not Lying Now; Forget Lie They Got Caught In Already
Third, the data was exposed as early as 2013 and the OPM senior executives cooperated, de facto, with the hostile intelligence service by minimizing and concealing the extent and seriousness of the breach then. CNN again (emphasis ours):
The roots of the recent OPM breach could be traced to an earlier 2013 OPM breach, investigators now believe. At the time, OPM officials minimized what was taken by hackers, who are believed to be the same responsible for the latest breach. But it turned out what was taken provided blueprints to the OPM network, valuable information for future intruders.
At Wednesday’s House Oversight hearing, Donna Seymour, the agency’s chief information officer, said that in the 2013 breach, hackers took “some manuals about our systems.”
Asked if those manuals were akin to blueprints of OPM’s computer systems, Seymour answered, “It would be fair to say that would give you enough information that you could learn about the platform, the infrastructure of our system, yes.”
Seymour called it a breach of security.
But that contrasts with earlier statements by OPM officials.
What do you think… are they lying now, or were they lying then? Does what we should do with them change based on the answer to this question? (What should we do with them? And should it involve tar, feathers, fire, a trebuchet, and easy assembly instructions?)
In a 2014 interview with WJLA-TV in Washington about the 2013 breach, Archuleta minimized the damage.
“I can tell you the most important piece: No personal identification information was compromised,” she said. “That’s the most important thing. That happened because of the good work and dedication of our employees.”
About the 2013 breach, Archuleta added: “Again, we did not have a breach in security. There was no information that was lost. We were confident as we worked through this that we would be able to protect the data.”
She’s right about one thing: this has happened because of the good work and dedication of her and her employees. Although we’re not sure what the adjective “good” is doing in there.
But it now looks like they didn’t just minimize the response. They deliberately misrepresented the scope and scale of the compromise, according to the Wall Street Journal (requisite Google Search if you’re paywalled out).
The Obama administration for more than a week avoided disclosing the severity of an intrusion into federal computers by defining it as two breaches but divulging just one, said people familiar with the matter.
But:
An OPM spokeswoman said the agency had been “completely consistent’’ in its accounting of the data breach.
Well, yeah, she and her agency have been completely consistent. They’ve consistently lied. Example? Here’s one from that same article:
A day after the public announcement, an OPM spokesman said there was “no evidence to suggest that information other than what is normally found in a personnel file has been exposed.’’ By that time, the FBI already knew—and told OPM—that security-clearance forms had been tapped, officials said.
You can tell when Archuleta and Co. lie. Their lips move.
4: Did You Hear The One About The Screwed-Up Response?
Fourth, when the OPM went to notify even the initial 4.2 million victims they admit having, they botched it all over again, using a wildly insecure and unverified email system. (Hardly a surprise. Most key OPM systems were and are running with no or self-generated encryption and signing certificates). According to Navy Live (an official DOD site):
OPM began conducting notifications to affected individuals using email and/or USPS First Class mail on June 8, 2015. Recognizing the inherent security concerns in this methodology, with OPM and CSID support, DoD suspended notifications to employees on June 11, 2015, until an improved, more secure notification and response process is in place. Late June 15, 2015, OPM advised that email notification resumed. Email notifications should be complete by June 22, 2015. U.S. Postal mail notifications will take longer.
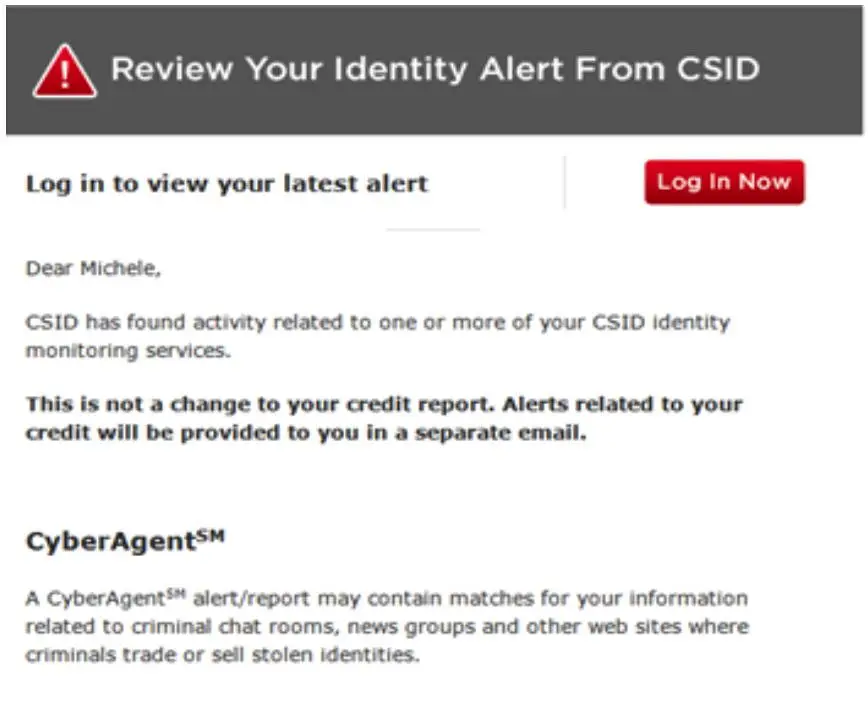
By the way, here’s what an email fraud alert for the crapola lowest-bidder “credit monitoring” service OPM bought no-bid from some crony and is force-feeding to victims looks like:
Yeah, just like a Nigerian scam!
Are that company’s servers as secure as OPM’s (which is to say, not terribly?) Or do you just get hacked yourself if you’re dumb enough to click the Log In Now button in a shady-smelling email like this? Click that red button and you may just find out. (Not here of course. Here it is just a harmless picture. We think).
5: FLEOA’s Recommendation Doesn’t Work
Fifth, here is what is happening when federal Special Agents, intelligence agency staff and contractors, and other cleared personnel call up the credit bureaux about their records, they’re getting blown off. As one disillusioned Fed put it to us:
The credit companies have so many calls from government employees for fraud alerts that they want you to go online and do it. They do not want your call.
At first, the staff at Experian, TransUnion, etc., may have fielded the calls personally, but soon the party line was “Don’t waste time on Federal employees and contractors.” Those unfortunates should not expect personal service; after all, the credit resellers aren’t getting paid for helping victims of enemies foreign (hackers) and domestic (OPM brass). Instead, some outfit you never heard of got a huge no-bid contract to further surveil you. (Wonder if there’s a kickback to the OPM panjandrums).
“Hang up and order a credit report online.” Click.
Soon, the firms’ initial voicemail menus were changed to cut hack victims off before even getting to that point. When you dial in, before you get the voice menu, you’re told not to bother calling the telephone line, if you’re an OPM victim. They can’t stop you from getting your one statutory credit report per year, but they can make it as difficult as they like — and they do.
The Bottom Line
OPM, after doing just about everything they could do to give away the security data, now is finger-pointing, to the extent it’s doing anything. (Hey, you can’t interfere with the 10 AM-3 PM Federal workday with a two-hour lunch. That’s an entitlement for these drones). They haven’t even updated their own data breach information page since the 23rd — two full days ago.
Director Archuleta seems to think that these so-called “workers” are more useful to the taxpayers than the same number of empty chairs. Where’s the evidence for that proposition?
She also thinks that OPM has been a good steward of secret and sensitive information. On which planet, in which galaxy, does this remarkable condition obtain? Not, we submit, on ours.
She has decided, to the extent this idle bag of suet decides anything, that what the OPM really needs to recover from this Grand Slam of Beltway hackery is to hire another Beltway tusker, to be called a “Cybersecurity Advisor.”
Sounds like a job for Jamie Gorelick.

Kevin was a former Special Forces weapons man (MOS 18B, before the 18 series, 11B with Skill Qualification Indicator of S). His focus was on weapons: their history, effects and employment. He started WeaponsMan.com in 2011 and operated it until he passed away in 2017. His work is being preserved here at the request of his family.



19 thoughts on “Five Depressing Developments on the OPM Data Compromise”
“(What should we do with them? And should it involve tar, feathers, fire, a trebuchet, and easy assembly instructions?)”
No, it should involve rope and lampposts.
“Sounds like a job for Jamie Gorelick.” I am laughing and crying (or crying laughing) at the same time. Jamie Gorelick, the MISTRESS of DISASTER! This debacle has her name laser etched on steel for this disaster. Thank you for the comedy…perfect timing! I am past the anger stage, now on to mocking anything and everything about these incompetents.
It’s time for Ms Archuleta to retire with a 100% stress related (Tax Free) disability.
No, it’s time for these criminals to retire with rope burns on their necks, the penalty for treason is a good hanging, not a lifetime pension at taxpayer expense.
Here’s the bottom line to all the OPM violations that allowed the theft of personal information….not ONE head will swing at fedgov’s Office of Personnel Management !
It is symptomatic of fedgov/stategov/localgov….while those within the .gov bureaucracies continually give the American serf an anal reaming without courtesy of a reach-around, the overpaid, ruling elites, our masters, continue to dismiss the .gov wrongdoings. They won’t eat their own.
Aw, the poor wittle fed employees are being blown off by the credit bureaus! Good! Now they know what it feels like to deal with a nameless, faceless federal employee of some useless federal agency.
But don’t you dare think that those political appointees and their permanent moles within the defense establishment are illegitimate, not for one moment because only nihilistic neo -nazis like Haxo would dare say such a thing
Rumors abound that the official salute shall involve lube only if you pass your politically reliability test. Enjoy your 4th Patriots
I don’t get it. People are acting as if the outing of federal employees, and their subsequent difficulties, is a bad thing.
It’s not just the federal employees. It’s active duty military as well.
And, it’s the personal information collected about any people used as references and whatever other personal information was developed by the investigators.
It’s therefore possible the even your personal information is now known to the intelligence services of any and all malign foreign governments if anyone you may know has, or had a security clearance and used you for a reference, whether or not you were even contacted by the FIS.
How’s that working for ya?
Good to see that you are in favor of the Communist government of China.
Always helpful to know where one’s true loyalties lie.
Whoah Hayabusa….since the turn of the century in 2000, the FUSA has developed a 3 TRILLION dollar trade deficit courtesy of Bill Clinton, the Republican-controlled Congress and the morons one calls their “fellow Americans”.
Buy anything made in Red China Hayabusa ? But in your defense….one cannot even find paperclips made in this country.
Be careful challenging one’s loyalties, for the POTUS since Tricky Dick thru the usurping soetoro-obama have been fellating the ChiComs. Or perhaps you didn’t know that ?
Random thoughts…
What I’m wondering is if the Chinese may have succeeded a bit too well, i.e., if they have absconded with too much info to really be useful from an intelligence perspective? I mean, let’s go with the figure of 18 million SF86s or equivalent, and let’s say that each SF86 runs to, on average, 100+ pages. That works out to somewhere in the neighborhood of two billion pages of information. How the hell are they going to analyze all that and sift the useful intelligence leads from the hundreds of millions of pages of useless administrative chaff?
If I were the Chinese, I guess the information I’d be most interested in would be the foreign contact info, especially the social friends and love interests of USG personnel who have been posted to the embassy or one of the consulates in China. Knowing which Chinese citizens cleared USG personnel have been friendly with, or romantically involved with, would be a gold mine from both the counter-intelligence and espionage recruitment standpoints. Maybe they have some sort of algorithm that lets them sift that sort of info out of billions of pages of information. I don’t know.
Because they already know the positions and people with knowledge they want to exploit now. They now have a base of info on who they want to collect against in the future. Too much info? Not really when you think of it in terms of an organized file drawer. It’s not the personal info lost that is the problem it’s the increased possibility of exploitation of current and future targets that is the issue.
And, of course, we’re going to totally screw the opportunity to fuck with their heads using this.
Instead of the “Aw, shuckee-darn, we done fucked up…” thing that the idiots have been doing, what they should have done was just grin and bare it out for us, and tell the world “Yes, we have this problem, but we did it as a counter-intelligence operation, and salted the living hell out of that database with honeypots, traps, and false data designed to catch anyone trying to use it to recruit US citizens…
And, we should have used it to plant false stories, like that the head of Chinese counter-intelligence is having a long-term relationship with one of our agents…
Played right, this was an opportunity. We’re not smart enough to do that, however-Just like I would have used both Snowden and Manning as similar opportunities to confuse the shit out of foreign agencies. Ideally, we should have used Manning’s revelations as an opportunity to tell the world that we completely penetrated al Qaeda, and had operatives running at the highest levels of the organization. And, then watched as they all killed each other for us. Same-same with Snowden.
Nobody on our side is either imaginative or smart enough to pull something like this off, however. So, we’re fucking boned.
Oh the imagination and smarts are there…but the balls to sign off on such a thing are long gone.
And the fedgov is happy to eat its own, as long as its the icky defense types. Those dummies signed up for this stuff after all, who cares if they lose their money and ID and livelyhood, after all the gov has already dumped their benefits, let them die waiting for earned medical care for conditions and diseases 20yrs of service gave them, and called them terrorist and racists and whatnot.
Why do military types generally end up conservatives? They see government inaction and incompetence in person almost daily.
People think this was a hack by the Chinese. No it wasn’t… It was perpetrated by our own government to coincide with the economic collapse orchestrated for this Fall 2015. Once the dollar is crushed and revalued or replaced, single monetary system or cashless system (NWO); it does not matter what kind of credit you had its what’s in store for those who refuse to accept it. What gets me is that the three major credit reporting agencies are not and have not been hacked. How can that luciferian system remain untouched? Why? Because it’s controlled by the same elitists who enslave you with debt. THE BANKSTERS! How the hell can you say that someone who is insolvent (FICO credit rating and in debt) is far better off than someone who is solvent, believes in paying cash for everything. Or what is considered currency (fiat) versus money (gold or silver). This is a 32-million personnel sideshow! This, if anything, is to root out those who would oppose a cashless society or better yet those who believe in a system that is backed by gold or silver and not fiat. Why the hell are the credit reporting agencies not hacked? Is that system secured far greater than legitimate the federal government system, or some defense contractor or…shit our own systems have been culled, reaped, harvested over, look what the Chinese already have in defense. They have been given intellectual property already by several administrations. Crap, the economic collapse this Fall will be far more catastrophic than what the Chinese and foreigners already know. The we are among other nations of debtors and the new slave masters will be the elitists who control it…if not already!!! Conspiracy? Well what the hell do you call it… When a group of people “conspire” to take your fiat imaginary currency, which can be seen and turn it into just a bunch of electronic numbers (cashless) system. Again, this is a sideshow to distract the majority, from what’s to come. The true distribution of wealth will be the one out ten who prepared for this event horizon!
Can’t tell if this is satire or not; if so, well done.
If not, watch out: the black helicopters are coming for YOU!
They ain’t black. You just can’t tell them apart from any other choppa!
“Instead, some outfit you never heard of got a huge no-bid contract to further surveil you. (Wonder if there’s a kickback to the OPM panjandrums).”
And this never heard of before outfit, sub-contracts out work… A man by the name of Lee is on the board of the subcontractor and is being investigated by the DOJ for a fund he ran where 99% of the $60 million fund, just disappeared!!!
You just can’t make this chit up
Thank you ChainYaMongrel.
I almost thought the aluminium hat chorus had disbanded or gone to Reddit and abandoned the rest of us, we who can’t see what’s really happening.
Not that I don’t think there aren’t people trying to make the world over into something they prefer. The Koch boys may not be the Illuminati, bur they’ll keep us entertained for a while.
The Chinese, past masters of power-grabbing intrigue and political ruthlessness, are eating our lunch in Asia and Africa, funding and building railroads, highways and hydroelectric dams, not to mention building military bases in the middle of the South China Sea.
Our government can’t even protect their databases from getting hacked.
As much that has happened in my lifetime, the next 50 years is definitely going to be “interesting times.”